In the very first blog site of our series on Azure Security, we discussed our method to taking on cloud vulnerabilities. Our 2nd blog site highlighted our usage of alternative searching to identify patterns and boost security throughout our services. The 3rd blog site in the series presented game-changing architecture to enhance integrated security In this installation, we share our integrated action technique which offers a constant knowing design, leveraging huge information, to enhance action, detections, preventative controls, and governance to determine and enhance efficiency.
Azure Security’s “Integrated Action” is the function of including security threat mitigation methods into a resilient security program, flawlessly collaborating throughout federated security functions to discover, share, and adjust reliable methods to resolve leading dangers and risks at hyper-scale. As brand-new risks and security dangers emerge from a range of sources, we resolve them by examining origin and establishing security controls as a knowing feedback system. Our knowings from proactive and reactive analysis become item updates and hazard intelligence improvements in our security items.
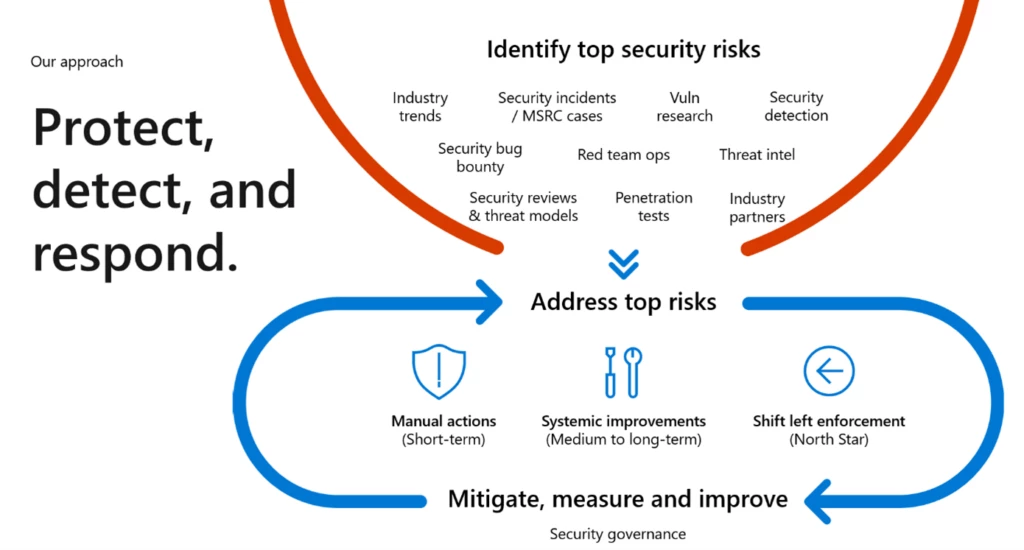
To preserve trust and speed up action timelines, our closed-loop feedback cycle integrates both internal and external threat chauffeurs to enhance each phase of our security action pipeline. Routinely evaluating security occurrences is crucial to our capability to constantly enhance our dexterity and action time to alleviate security dangers for our consumers. Each of our institutional procedures, such as the Security LiveSite Evaluation (SLR), Security Health Reviews (SHR), and our Security Operation Evaluations (SOR) emphasize and focus on chances for enhancement at all levels of Azure’s engineering companies. Let’s dive into what each of these stages implies and how they link to each other.
Promoting a safe and secure culture: A much deeper take a look at Azure’s extensive detailed defense and action
In a Cloud-First world, our consumers trust us with their information, copyright, and important organization applications. To satisfy these expectations, we take a holistic method to govern security and produce an Integrated Action which integrates a feedback cycle of determining threat chauffeurs and guaranteeing we drive the suitable security controls to correctly secure, identify and react to risks. In addition, we make sure all items satisfy our security requirements, such as Microsoft Cloud Security standards. Here are the parts of our Integrated Action:
Very first action on brand-new risks: Microsoft Security Action Center (MSRC) and Cyber Defense Operations— Running with an “Presume Breach” state of mind, we have actually developed our capability to rapidly and efficiently react to security occurrences and drive quick security mitigation and enhancements. We engage consumers, market partners, and Microsoft item groups alike to operate in this constant feedback loop. MSRC is an integrated part of the protector neighborhood operating on the cutting edge of security action for our Azure consumers and for other items within Microsoft. For more than twenty years, MSRC has actually served to identify, react, and recuperate from security vulnerabilities. Our years of experience protecting a large range of innovations have actually revealed us that continuously finding out and developing, both in and out, is vital to remaining ahead of the ever-changing hazard landscape.
Gain From every Security Event: Security Live Website Evaluations (SLR)— Following a security event stemming from MSRC or Red Group Operations, after the instant removal activity concludes, we focus on carrying out SLRs to drive 5-why analysis with item groups and executive management. Deeply focusing each and every single week from the Executive VP level down on deconstructing occurrences to their contributing source( s) drives Microsoft’s methods on determining procedure spaces, security control updates, and item enhancements to enhance Azure’s security posture. As talked about previously in the series, throughout the examination, we recognize extra patterns beyond the particular event to guarantee we resolve beyond the sign to the holistic option. We track these repair work products through all stages of our product or services advancement lifecycle consisting of operations, engineering workflow, and security governance procedures.
Make sure security culture and enhance functional rigor: Security Operations Evaluation (SOR)— To enhance security for functional health and cultivate a deep security culture, we perform routine SOR. These evaluations combine executive leaders and item groups to share finest practices and evaluation behavioral patterns, security control efficiency, and show a shown capability to preserve security SLAs as a proactive procedure.
Understand and decrease holistic security threat: Security Health and Danger Reviews (SHR)— Comprehending the security threat of numerous requirements are an essential aspect to preserving a correct security-first state of mind. We justify control efficiency and threat in the aggregate to perform deep dives with item groups, producing a joint security-review discussion to discover and drive methods to resolve emerging risks more broadly. The SHR offers a deep link to emerging threat by combining Azure Security point of views with tactical item enhancements to guarantee we satisfy our consumers’ requirements now and into the future, offering self-confidence that we are buying groundbreaking security development for tomorrow’s risks.
Govern efficiently and drive security requirements: Azure Security Governance— Constantly following a development state of mind, we drive security governance at scale throughout more than 6 thousand special items, driving security standard compliance, guaranteeing our consumers have the best security abilities incorporated into our items prior to release as recorded in Microsoft Cloud Security Standard (MCSB), which assists consumers guarantee their service setups of Azure and other clouds satisfy the security spec specified in structures such as the Center for Web Security, the National Institute of Standards and Innovation, and the Payment Card Market. MCSB offers an effective positioning method for consumers to utilize as controls are pre-mapped to these market standards.
Internally, this governance function steps and offers insights and patterns around behavioral and security control efficiency throughout our items, incorporating brand-new controls in SDL to remain pertinent and mitigating emerging dangers, while likewise empowering leaders with security optics to assist them comprehend their security posture and drive security-first culture within their groups. We track security crucial efficiency Indicators (KPIs), at scale, and focus on controls reliable at reducing risks based upon real-world findings from source analysis of harmful attacks, RED Group discovery, MSRC findings, and market occurrences. Numerous are broadly recognized as the market’s finest practices and requirements of Microsoft Security Policy (SDL/OSA) in addition to regulative compliance requirements. These security KPIs are determined with Microsoft security innovations which have actually broadened and grown gradually.
Accepting consistent knowing: How Azure’s Integrated Action technique innovates security for an altering world
Our Integrated Action technique offers a holistic method to include threat chauffeurs with security controls and make sure items satisfy Microsoft Cloud Security standards, leveraging measurement at scale and governance to recognize and alleviate dangers end-to-end. Microsoft integrates our strong internal security action program with a broad and varied environment of security partners to provide first-rate defense for billions of consumers and the wider market. We acknowledge that security is a conclusion of item and procedure which Defense-in-Depth is a layered method to both. As such, we welcome feedback and repeat enhancements by determining for result. Our years of experience protecting a large range of innovations have actually revealed us that continuously finding out and developing, both in and out, is vital to remaining ahead of the ever-changing hazard landscape.
Discover More
- Check out extra blog sites in this series to discover how Azure leverages cloud alternative searching, safe multitenancy, Confidential Compute, and Rust to layer defense throughout every stage of style, advancement, and implementation.