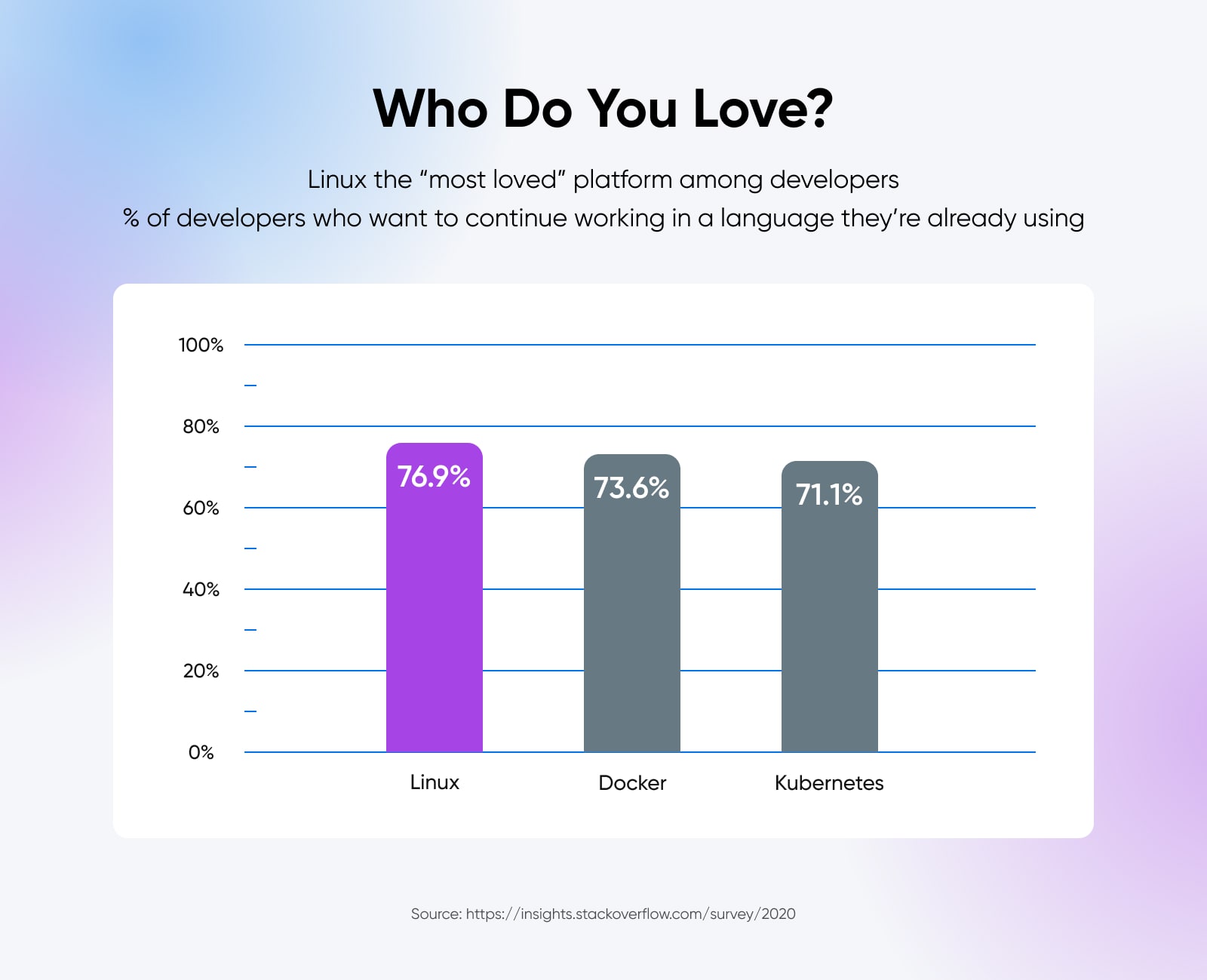
Linux is the spine of the web. It powers just about 97% of the arenaâs best internet servers. And 55.9% {of professional} builders lean on Linux for his or her building wishes.
But, Linux has just a 2.68% desktop marketplace proportion. Why this hole?
The core center of attention of Linux hasn’t ever been its person interface. It was once as an alternative designed to come up with entire regulate over your working formulation throughout the command line.
That may make Linux appear intimidating to novices â And the hundreds of to be had instructions simplest make this tougher.
On this article, we duvet the highest 100 most precious Linux instructions. Finding out only a handful of those instructions let you spice up your productiveness as a Linux person. Letâs dive proper in!
Linux
Linux refers to a number of open-source Running Methods (OS). Thereâs no unmarried Linux OS. As a substitute, customers can choose between a wide crew of Linux distros, all of which offer other reviews.
What Are Linux Instructions?
Linux instructions will let you regulate your formulation from the command line interface (CLI) as an alternative of the usage of your mouse or trackpad. They’re textual content directions entered into the terminal to inform your formulation precisely what to do.
Instructions you input at the Linux terminal are case-sensitive and apply a syntax like âcommand -options arguments.â You’ll mix them for complicated duties the usage of pipelines and redirection.
Some key issues to find out about Linux instructions:
- They’re case-sensitive; as an example, â
lsâ and âLSâ imply various things. - They apply a selected syntax like â
command -options arguments.â - They may be able to be mixed for complicated operations the usage of pipelines and redirection.
- They come up with fine-grained regulate over your formulation, which is difficult to reach with graphical interfaces.
- They will let you automate duties thru shell scripts and batch processing.
- They may be able to be used to get admission to formulation sources just like the dossier formulation, community, reminiscence, and CPU.
- They shape the root of interplay with Linux servers and working methods.
If you happen toâre a programmer thatâs simply finding out to code, you’ll birth working towards your Linux instructions with out leaving Home windows the usage of the Home windows Subsystem for Linux. This permits you to run Linux from inside Home windows with out twin booting and get the most productive of each working methods.
Best 100 Maximum Helpful Linux Instructions
Now that you’ve got a elementary working out of what Linux instructions are, letâs dive into the highest 100 maximum recurrently used Linux instructions.
Weâve arranged them through class to hide spaces like dossier control, formulation tracking, community operations, person management, and extra.
Record Control Instructions In Linux
Record control is a commonplace activity at the Linux command line. Listed below are very important dossier instructions:
1. ls â Checklist Listing Contents
The ls command is likely one of the maximum continuously used Linux instructions. It lists the contents of a listing, appearing all information and subdirectories contained inside of.
With none suggestions or arguments, ls will show the contents of the present operating listing. You’ll cross a trail identify to record information and folders in that location as an alternative.
Syntax:
Â
One of the vital most precious ls suggestions come with:
-lâ Show ends up in lengthy structure, appearing additional main points like permissions, possession, measurement, and amendment date for every dossier and listing.-aâ Display hidden information and directories that birth with . along with non-hidden pieces.-Râ Recursively record all subdirectory contents, descending into kid folders indefinitely.-Sâ Type effects through dossier measurement, greatest first.-tâ Type through timestamp, latest first.
Instance:
ls -l /house/person/paperwork |
This might record the contents of the âpaperworkâ folder in lengthy structure.
Instance output:
overall 824-rwxrwx--- 1 person person    8389 Jul 12 08:53 document.pdf-rw-r--r-- 1 person person   10231 Jun 30 16:32 presentation.pptxdrwxr-xr-x 2 person person    4096 Would possibly 11 09:21 pictures-rw-rw-r-- 1 person person     453 Apr 18 13:32 todo.txt |
This output displays an in depth record with permissions, measurement, proprietor, and timestamp for every dossier and listing. The lengthy checklist structure given through the -l choice supplies useful dossier knowledge at a look.
The ls command will give you versatile regulate over listing content material checklist. Itâs one of the crucial instructions youâll in finding your self the usage of repeatedly when operating on Linux.
2. cd â Exchange Listing
The cd command is used to navigate between directories. It lets you transfer the present operating listing to a brand new location within the filesystem.
Whilst you run the cd command on its own, it’s going to go back you to the house listing. You’ll additionally cross a selected trail to become. As an example:
cd /usr/nativeâ Adjustments to the /usr/native listing.cd ..â Strikes up one degree to the dad or mum listing.cd ~/photosâ Adjustments to the photographs folder in your house listing.
Syntax:
cd [directory]
Instance:
cd /house/person/paperwork
This might alternate the operating listing to the âpaperworkâ folder beneath /house/person. The use of cd is very important for with the ability to get admission to and paintings with information in numerous places with ease.
3. mkdir â Create A New Listing
The mkdir command lets you create a brand new folder. You merely cross the identify of the listing to create.
Syntax:
mkdir [options] <listing>
This will likely create a listing referred to as ânewprojectâ within the present operating listing.
Some helpful mkdir suggestions:
-pâ Creates dad or mum directories recursively as wanted.-vâ Verbose output appearing created directories.
Instance:
mkdir -v ~/venture/code
This might create the âcodeâ subdirectory beneath âventureâ within the personâs house folder, with verbose output appearing the listing being created.
Get Content material Delivered Directly to Your Inbox
Subscribe to our weblog and obtain nice content material identical to this delivered immediately in your inbox.
4. rmdir â Take away Listing
To delete an empty listing, use the rmdir command. Word that rmdir can simplest take away empty directories â weâll want the rm command to delete non-empty ones.
Syntax:
rmdir [options] <listing>
Some suggestions for rmdir come with:
-vâ Verbose output when deleting directories.-pâ Take away dad or mum directories recursively as wanted.
Instance:
rmdir -v ~/venture/code
This might delete the âcodeâ subdirectory beneath âventureâ whilst appearing verbose output.
5. contact â Create A New Empty Record
The contact command is used to create a brand new empty dossier immediately. This comes in handy when you wish to have an empty dossier to populate with information later.
The elemental syntax of contact is:
contact [options] filename
Some helpful suggestions for contact come with:
-câ Don’t create the dossier if it already exists. This avoids by accident overwriting current information.-mâ As a substitute of constructing a brand new dossier, replace the timestamp on an current dossier. This can be utilized to switch the changed time.
As an example:
contact /house/person/newfile.txt
The above command creates a brand new empty dossier referred to as ânewfile.txtâ within the personâs /house/person listing. If newfile.txt already exists, it’s going to replace the get admission to and amendment occasions at the dossier as an alternative.
6. cp â Reproduction Recordsdata And Directories
The cp command copies information or directories from one location to some other. It calls for passing a supply trail and a vacation spot.
The elemental syntax of cp is:
cp [options] supply vacation spot
Some helpful cp suggestions:
-râ Reproduction directories recursively, descending into kid directories to replicate their contents as neatly. Vital when copying directories.-iâ Instructed ahead of overwriting any current information on the vacation spot. It prevents by accident overwriting information.-vâ Show verbose output appearing the main points of every dossier as it’s copied. Useful to substantiate precisely what was once copied.
As an example:
cp -r /house/person/paperwork /backups/
This might recursively reproduction the /house/person/paperwork listing and all its contents to the /backups/ listing. The -r choice is had to reproduction directories.
The cp command is likely one of the maximum continuously used dossier control utilities for copying information and directories in Linux. Youâll in finding your self the usage of this command fairly regularly.
7. mv â Transfer Or Rename Recordsdata And Directories
The mv command is used to transport information or directories to another location or rename them. In contrast to reproduction, the information from the supply trail are deleted when theyâve been moved to the vacation spot.
You’ll additionally use the mv command to rename information because you merely wish to alternate the supply and vacation spot paths to the previous and new identify.
The syntax of mv is:
mv [options] supply vacation spot
Helpful mv suggestions:
-iâ Instructed ahead of overwriting any current information on the vacation spot location. This prevents by accident overwriting information.-vâ Produce verbose output appearing every dossier or listing as it’s moved. That is useful for confirming precisely what was once moved.
As an example:
mv ~/folder1 /tmp/folder1
The above will transfer folder1 from the house (~) listing to the /tmp/ listing. Letâs have a look at some other instance of the usage of the mv command for renaming information.
mv folder1 folder2
Right here, âfolder1â is renamed to âfolder2.â
8. rm â Take away Recordsdata And Directories
The rm command deletes information and directories. Use warning as a result of deleted information and directories can’t be recovered.
The syntax is:
rm [options] identify
Helpful rm suggestions:
-râ Recursively delete directories, together with all contents inside of them. That is essential when deleting directories.-fâ Drive deletion and suppress all affirmation activates. It is a bad command, as information can’t be recovered after theyâre long past!-iâ Instructed for affirmation ahead of deleting every dossier or listing, which supplies protection towards unintended elimination.
As an example:
rm -rf temp
This recursively deletes the âtempâ listing and all its contents with out prompting (-f overrides confirmations).
Word: The rm command completely erases information and folders, so use it with excessive care. If used with sudo privileges, you’ll want to additionally delete the basis listing utterly, and Linux would not serve as after restarting your pc.Â
9. in finding â Seek For Recordsdata In A Listing Hierarchy
The in finding command recursively searches directories for information matching given standards.
The elemental syntax of in finding is:
in finding [path] [criteria]
Some helpful standards suggestions for in finding come with:
-type fâ Seek for simplest standard information, omitting directories.-mtime +30â Seek for information changed over 30 days in the past.-user janeâ Seek for information belonging to person âjane.â
As an example:
in finding . -type f -mtime +30
This will likely in finding all common information over 30 days previous beneath the present listing (denoted through the dot).
The in finding command permits in search of information in keeping with a wide variety of complex prerequisites like identify, measurement, permissions, timestamps, possession, and extra.
10. du â Estimate Record House Utilization
The du command measures the dossier house utilization for a given listing. When used with out suggestions, it shows disk utilization for the present operating listing.
The syntax for du is:
du [options] [path]
Helpful du suggestions:
-hâ Show dossier sizes in human-readable structure like Okay for Kilobytes relatively than a byte depend. A lot more uncomplicated to parse.-sâ Simplest display the overall measurement for a listing, relatively than checklist every subdirectory and dossier. Just right for abstract.-aâ Display person dossier sizes along with totals. Is helping establish huge information.
As an example:
du -sh photos
This will likely print a human-readable measurement overall for the âphotosâ listing.
The du command is beneficial for inspecting disk utilization for a listing tree and figuring out information eating over the top house.
Seek And Clear out Instructions In Linux
Now, letâs discover instructions that will let you seek, filter out, and manipulate textual content proper from the Linux command line.
11. grep â Seek Textual content The use of Patterns
The grep command is used to seek for textual content patterns inside information or output. It prints any strains that fit the given common expression. grep is terribly robust for looking out, filtering, and trend matching in Linux.
This is the fundamental syntax:
grep [options] trend [files]
As an example:
grep -i "error" /var/log/syslog
This searches the syslog dossier for the phrase âerror,â ignoring case sensitivity.
Some helpful grep suggestions:
-iâ Forget about case distinctions in patterns-Râ Recursively seek subdirectories-câ Print just a depend of matching strains-vâ Invert fit, print non-matching strains
grep lets you seek information and output for key phrases or patterns temporarily. Itâs beneficial for parsing logs, looking out supply code, matching regexes, and extracting information.
12. awk â Trend Scanning And Processing Language
The awk command permits extra complex textual content processing in keeping with specified patterns and movements. It operates on a line-by-line foundation, splitting every line into fields.
awk syntax is:
awk 'trend { motion }' input-file
As an example:
awk '/error/ {print $1}' /var/log/syslog
This prints the primary box of any line containing âerror.â awk too can use integrated variables like NR (collection of information) and NF (collection of fields).
Complicated awk functions come with:
- Mathematical computations on fields
- Conditional statements
- Integrated purposes for manipulating strings, numbers, and dates
- Output formatting regulate
This makes awk appropriate for information extraction, reporting, and remodeling textual content output. awk is terribly robust since it’s an unbiased programming language supplying you with numerous regulate as a Linux command.
13. sed â Movement Editor For Filtering And Reworking Textual content
The sed command permits filtering and transformation of textual content. It may well carry out operations like seek/substitute, deletion, transposition, and extra. On the other hand, not like awk, sed was once designed for enhancing strains on a per-line foundation as according to the directions.
Right hereâs the fundamental syntax is:
sed suggestions 'instructions' input-file
As an example:
sed 's/foo/bar/' dossier.txt
This replaces âfooâ with âbarâ in dossier.txt.
Some helpful sed instructions:
sâ Seek and substitute textual content/trend/dâ Delete strains matching a trend10,20dâ Delete strains 10-201,3!dâ Delete all aside from strains 1-3
sed is perfect for duties like bulk in finding/substitute, selective line deletion, and different textual content movement enhancing operations.
14. type â Type Strains Of Textual content Recordsdata
Whilst youâre operating with numerous textual content or information and even huge outputs from different instructions, sorting this can be a nice method to make issues manageable. The type command will type the strains of a textual content dossier alphabetically or numerically.
Elementary type syntax:
type [options] [file]
Helpful type suggestions:
-nâ Type numerically as an alternative of alphabetically-râ Opposite the type order-kâ Type in keeping with a selected box or column
As an example:
type -n grades.txt
This numerically varieties the contents of grades.txt. type is to hand for ordering the contents of information for extra readable output or research.
15. uniq â Record Or Forget Repeated Strains
The uniq command filters reproduction adjoining strains from enter. That is regularly used at the side of type.
Elementary syntax:
uniq [options] [input]
Choices:
-câ Prefix distinctive strains with depend of occurrences.-dâ Simplest display duplicated strains, now not distinctive ones.
As an example:
type information.txt | uniq
This will likely take away any duplicated strains in information.txt after sorting. uniq will give you regulate over filtering repeated textual content.
16. diff â Evaluate Recordsdata Line By means of Line
The diff command compares two information line-by-line and prints the variations. Itâs recurrently used to turn adjustments between variations of information.
Syntax:
diff [options] file1 file2
Choices:
-bâ Forget about adjustments in whitespace.-Bâ Display variations inline, highlighting adjustments.-uâ Output variations with 3 strains of context.
As an example:
diff authentic.txt up to date.txt
This will likely output the strains that vary between authentic.txt and up to date.txt. diff is beneficial for evaluating revisions of textual content information and supply code.
17. wc â Print Line, Phrase, And Byte Counts
The wc (phrase depend) command prints counts of strains, phrases, and bytes in a dossier.
Syntax:
wc [options] [file]
Choices:
-lâ Print simplest the road depend.-wâ Print simplest the phrase depend.-câ Print simplest the byte depend.
As an example:
wc document.txt
This command will print the collection of strains, phrases, and bytes in document.txt.
Redirection Instructions In Linux
Redirection instructions are used to regulate enter and output resources in Linux, permitting you to ship and append output streams to information, take enter from information, attach a couple of instructions, and break up output to a couple of locations.
18. > â Redirect Same old Output
The > redirection operator redirects the usual output movement from the command to a dossier as an alternative of printing to the terminal. Any current contents of the dossier shall be overwritten.
As an example:
ls -l /house > homelist.txt
This will likely execute ls -l to record the contents of the /house listing.
Then, as an alternative of printing that output to the terminal, the > image captures that ordinary output and writes it to homelist.txt, overwriting any current dossier contents.
Redirecting usual output is beneficial for saving command effects to information for garage, debugging, or chaining instructions in combination.
19. >> â Append Same old Output
The >> operator appends usual output from a command to a dossier with out overwriting current contents.
As an example:
tail /var/log/syslog >> logfile.txt
This will likely append the ultimate 10 strains of the syslog log dossier onto the tip of logfile.txt. In contrast to >, >> provides the output with out erasing the present logfile.txt contents.
Appending is beneficial in accumulating command output in a single position with out dropping current information.
20. < â Redirect Same old Enter
The < redirection operator feeds a dossierâs contents as usual enter to a command, as an alternative of taking enter from the keyboard.
As an example:
wc -l < myfile.txt
This sends the contents of myfile.txt as enter to the wc command, which is able to depend strains in that dossier as an alternative of looking ahead to keyboard enter.
Redirecting enter comes in handy for batch-processing information and automating workflows.
21. | â Pipe Output To Any other Command
The pipe | operator sends the output from one command as enter to some other command, chaining them in combination.
As an example:
ls -l | much less
This pipes the output of ls -l into the fewer command, which permits scrolling throughout the dossier checklist.
Piping is recurrently used to chain in combination instructions the place the output of 1 feeds the enter of some other. This permits development complicated operations out of smaller single-purpose methods.
22. tee â Learn From Same old Enter And Write To Same old Output And Recordsdata
The tee command splits usual enter into two streams.
It writes the enter to plain output (displays the output of the primary command) whilst additionally saving a duplicate to a dossier.
As an example:
cat dossier.txt | tee reproduction.txt
This shows dossier.txt contents to the terminal whilst concurrently writing it to replicate.txt.
tee is not like redirecting, the place you donât see the output till you open the dossier youâve redirected the output to.
Archive Instructions
Archiving instructions will let you package a couple of information and directories into compressed archive information for more uncomplicated portability and garage. Commonplace archive codecs in Linux come with .tar, .gz, and .zip.
23. tar â Retailer And Extract Recordsdata From An Archive
The tar command is helping you’re employed with tape archive (.tar) information. It is helping you package a couple of information and directories right into a unmarried compressed .tar dossier.
Syntax:
tar [options] filename
Helpful tar suggestions:
-câ Create a brand new .tar archive dossier.-xâ Extract information from a .tar archive.-fâ Specify archive filename relatively than stdin/stdout.-vâ Verbose output appearing archived information.-zâ Compress or uncompress archive with gzip.
As an example:
tar -cvzf pictures.tar.gz /house/person/pictures
This creates a gzip-compressed tar archive referred to as pictures.tar.gz containing the /house/person/pictures folder.
24. gzip â Compress Or Make bigger Recordsdata
The gzip command compresses information the usage of LZ77 coding to cut back measurement for garage or transmission. With gzip, you’re employed with .gz information.
Syntax:
gzip [options] filename
Helpful gzip suggestions:
-câ Write output to stdout as an alternative of dossier.-dâ Decompress dossier as an alternative of compacting.-râ Recursively compress directories.
As an example:
gzip -cr paperwork/
The above command recursively compresses the paperwork folder and outputs to stdout.
25. gunzip â Decompress Recordsdata
The gunzip command is used for decompressing .gz information.
Syntax:
gunzip filename.gz
Instance:
gunzip paperwork.tar.gz
The above command will extract the unique uncompressed contents of paperwork.tar.gz.
26. zip â Bundle And Compress Recordsdata
The zip command creates .zip archived information containing compressed dossier contents.
Syntax:
zip [options] archive.zip filenames
Helpful zip suggestions:
-râ Recursively zip a listing.-eâ Encrypt contents with a password.
Instance:
zip -re pictures.zip photos
This encrypts and compresses the photographs folder into pictures.zip.
27. unzip â Extract Recordsdata From ZIP Archives
Very similar to gunzip, the unzip command extracts and uncompresses information from .zip archives.
Syntax:
unzip archive.zip
Instance:
unzip pictures.zip
The above instance command extracts all information from pictures.zip within the present listing.
Record Switch Instructions
Record switch instructions will let you transfer information between methods over a community. This comes in handy for copying information to faraway servers or downloading content material from the web.
28. scp â Protected Reproduction Recordsdata Between Hosts
The scp (safe reproduction) command copies information between hosts over an SSH connection. All information switch is encrypted for safety.
scp syntax copies information from a supply trail to a vacation spot outlined as person@host:
scp supply person@host:vacation spot
As an example:
scp symbol.jpg person@server:/uploads/
This securely copies symbol.jpg to the /uploads folder on server as person.
scp works just like the cp command however for faraway dossier switch. It leverages SSH (Protected Shell) for information switch, offering encryption to be sure that no touchy information, similar to passwords, are uncovered over the community. Authentication is normally treated the usage of SSH keys, although passwords may also be used. Recordsdata can also be copied each to and from faraway hosts.
29. rsync â Synchronize Recordsdata Between Hosts
The rsync software synchronizes information between two places whilst minimizing information switch the usage of delta encoding. This makes it quicker to sync huge listing bushes.
rsync syntax syncs supply to vacation spot:
rsync [options] supply vacation spot
As an example:
rsync -ahv ~/paperwork person@server:/backups/
The above instance command recursively syncs the paperwork folder to server:/backups/, appearing verbose, human-readable output.
Helpful rsync suggestions:
-aâ Archive mode syncs recursively and preserves permissions, occasions, and many others.-hâ Human-readable output.-vâ Verbose output.
rsync is perfect for syncing information and folders to faraway methods and maintaining issues decentrally sponsored up and safe.
30. sftp â Protected Record Switch Program
The sftp program supplies interactive dossier transfers over SSH, very similar to common FTP however encrypted. It may well switch information to/from faraway methods.
sftp connects to a bunch then accepts instructions like:
sftp person@host
get remotefile localfile
put localfile remotefile
This retrieves remotefile from the server and copies localfile to the faraway host.
sftp has an interactive shell for navigating faraway dossier methods, moving information and directories, and managing permissions and houses.
31. wget â Retrieve Recordsdata from the Internet
The wget software downloads information over HTTP, HTTPS, and FTP connections. Itâs helpful for retrieving internet sources without delay from the terminal.
As an example:
wget https://instance.com/dossier.iso
This downloads the dossier.iso symbol from the faraway server.
Helpful wget suggestions:
-câ Resume interrupted obtain.-râ Obtain recursively.-Oâ Save to express filename.
wget is perfect for scripting computerized downloads and mirroring internet sites.
32. curl â Switch Information From Or To A Server
The curl command transfers information to or from a community server the usage of supported protocols. This comprises REST, HTTP, FTP, and extra.
As an example:
curl -L https://instance.com
The above command retrieves information from the HTTPS URL and outputs it.
Helpful curl suggestions:
-oâ Write output to dossier.-Iâ Display reaction headers simplest.-Lâ Apply redirects.
curl is designed to switch information throughout networks programmatically.
Record Permissions Instructions
Record permissions instructions will let you adjust get admission to rights for customers. This comprises atmosphere learn/write/execute permissions, converting possession, and default dossier modes.
33. chmod â Exchange Record Modes Or Get entry to Permissions
The chmod command is used to switch the get admission to permissions or modes of information and directories. The permission modes constitute who can learn, write, or execute the dossier.
As an example:
chmod 755 dossier.txt
There are 3 units of permissionsâproprietor, crew, and public. Permissions are set the usage of numeric modes from 0 to 7:
- 7 â learn, write, and execute.
- 6 â learn and write.
- 4 â learn simplest.
- 0 â no permission.
This units the landlord permissions to 7 (rwx), crew to five (r-x), and public to five (r-x). You’ll additionally reference customers and teams symbolically:
chmod g+w dossier.txt
The g+w syntax provides crew write permission to the dossier.
Atmosphere correct dossier and listing permissions is the most important for Linux safety and controlling get admission to. chmod will give you versatile regulate to configure permissions exactly as wanted.
34. chown â Exchange Record Proprietor And Crew
The chown command adjustments possession of a dossier or listing. Possession has two partsâthe person who’s the landlord, and the gang it belongs to.
As an example:
chown john:builders dossier.txt
The above instance command will set the landlord person to âjohnâ and the landlord crew to âbuilders.â
Simplest the basis superuser account can use chown to switch dossier house owners. Itâs used to mend permission issues through enhancing the landlord and crew as wanted.
35. umask â Set Default Record Permissions
The umask command controls the default permissions given to newly created information. It takes an octal masks as enter, which subtracts from 666 for information and 777 for directories.
As an example:
umask 007
New information will default to permissions 750 as an alternative of 666, and new directories to 700 as an alternative of 777.
Atmosphere a umask permits you to configure default dossier permissions relatively than depending on formulation defaults. The umask command comes in handy for proscribing permissions on new information with out depending on any individual stepping into and manually including restrictions.
Procedure Control Instructions
Those instructions will let you view, observe, and regulate processes operating in your Linux formulation. This comes in handy for figuring out useful resource utilization and preventing misbehaving methods.
36. playstation â Record A Snapshot Of Present Processes
The playstation command shows a snapshot of lately operating processes, together with their PID, TTY, stat, birth time, and many others.
As an example:
playstation aux
This displays each procedure operating as all customers with further main points like CPU and reminiscence utilization.
Some helpful playstation suggestions:
auxâ Display processes for all customers--forestâ Show tree of dad or mum/kid processes
playstation will give you visibility into whatâs lately operating in your formulation.
37. best â Show Linux Processes
The best command displays real-time Linux procedure knowledge, together with PID, person, CPU %, reminiscence utilization, uptime, and extra. In contrast to playstation, it updates the show dynamically to mirror present utilization.
As an example:
best -u mysql
The above command screens processes only for the âmysqlâ person. It turns into fairly useful in figuring out resource-intensive methods.
38. htop â Interactive Procedure Viewer
The htop command is an interactive procedure viewer changing the highest command. It displays formulation processes along side CPU/reminiscence/change utilization graphs, permits sorting through columns, killing methods, and extra.
Merely form in htop within the command line to view your processes.
htop has enhanced UI components with colours, scrolling, and mouse give a boost to for more uncomplicated navigation in comparison to best. Superb for investigating processes.
39. kill â Ship A Sign To A Procedure
The kill command sends a sign to a procedure to terminate or kill it. Indicators permit swish shutdown if the method handles them.
As an example:
kill -15 12345
The above command sends the SIGTERM (15) sign to prevent the method with PID 12345 gracefully.
40. pkill â Ship A Sign To A Procedure Based totally On Title
The pkill command kills processes through identify as an alternative of PID. It may well make issues more uncomplicated than discovering the PID first.
As an example:
pkill -9 firefox
This forcibly stops all Firefox processes with SIGKILL (9). pkill objectives processes through matching identify, person, and different standards as an alternative of the PID.
41. nohup â Run A Command Immune To Hangups
The nohup command runs processes resistant to hangups, so they retain operating when you sign off or get disconnected.
As an example:
nohup python script.py &
The above instance command will release script.py indifferent within the background and resistant to hangups. nohup is most often used to start out power background daemons and products and services.
Efficiency Tracking Instructions
Those instructions supply treasured formulation efficiency statistics to lend a hand analyze useful resource usage, establish bottlenecks, and optimize potency.
42. vmstat â Record Digital Reminiscence Statistics
The vmstat command prints detailed studies on reminiscence, change, I/O, and CPU task. This comprises metrics like reminiscence used/loose, change in/out, disk blocks learn/written, and CPU time spent on processes/idle.
As an example:
vmstat 5
Different helpful vmstat suggestions:
-aâ Display energetic and inactive reminiscence-sâ Show tournament counters and reminiscence stats-Sâ Output in KB as an alternative of blocks5â Output refreshed each 5 seconds.
The instance above outputs reminiscence and CPU information each 5 seconds till interrupted, which comes in handy for tracking are living formulation efficiency.
43. iostat â Record CPU And I/O Statistics
The iostat command screens and shows CPU usage and disk I/O metrics. This comprises CPU load, IOPS, learn/write throughput, and extra.
As an example:
iostat -d -p sda 5
Some iostat suggestions:
-câ Show CPU usage information-tâ Print timestamp for every document-xâ Display prolonged stats like provider occasions and wait counts-dâ Display detailed stats according to disk/partition as an alternative of combination totals-pâ Show stats for explicit disk units
This displays detailed per-device I/O stats for sda each 5 seconds.
iostat is helping analyze disk subsystem efficiency and establish {hardware} bottlenecks.
44. loose â Show Quantity Of Unfastened And Used Reminiscence
The loose command displays the overall, used and loose quantities of bodily and change reminiscence at the formulation. This provides an summary of to be had reminiscence.
As an example:
loose -h
Some suggestions for the loose command:
-bâ Show output in bytes-kâ Display output in KB as an alternative of default bytes-mâ Display output in MB as an alternative of bytes-hâ Print statistics in human-readable structure like GB, MB as an alternative of bytes.
This prints reminiscence statistics in human-readable structure (GB, MB, and many others). Itâs helpful when you need a snappy assessment of reminiscence capability.
45. df â Record Record Gadget Disk House Utilization
The df command shows disk house utilization for dossier methods. It displays the filesystem identify, overall/used/to be had house, and capability.
As an example:
df -h
The above command will print the disk usage in a human-readable structure. You’ll additionally run it with out arguments to get the similar information in block sizes.
46. sar â Gather And Record Gadget Job
The sar software collects and logs formulation task knowledge on CPU, reminiscence, I/O, community, and extra through the years. This knowledge can also be analyzed to spot efficiency problems.
As an example:
sar -u 5 60
This samples CPU utilization each 5 seconds for a length of 60 samples.
sar supplies detailed historic formulation efficiency information now not to be had in real-time gear.
Person Control Instructions
When the usage of multi-user methods, you could want instructions that allow you to handle customers and teams for get admission to regulate and permissions. Letâs duvet the ones instructions right here.
47. useradd â Create A New Person
The useradd command creates a brand new person account and residential listing. It units the brand new personâs UID, crew, shell, and different defaults.
As an example:
useradd -m john
Helpful useradd suggestions:
-mâ Create the personâs house listing.-gâ Specify the main crew as an alternative of the default.-sâ Set the personâs login shell.
The above command will create a brand new person, âjohn,â with a generated UID and residential folder created at /house/john.
48. usermod â Regulate A Person Account
The usermod command modifies the settings of an current person account. It will alternate the username, house dir, shell, crew, expiry date, and many others.
As an example:
usermod -aG builders john
With this command, you upload a person john to an extra crewââbuilders.â The -a appends to the present record of teams that the person is added to.
49. userdel â Delete A Person Account
The userdel command deletes a person account, house listing, and mail spool.
As an example:
userdel -rf john
Useful userdel suggestions:
-râ Take away the personâs house listing and mail spool.-fâ Drive deletion even though the person continues to be logged in.
This forces the elimination of person âjohn,â deleting related information.
Specifying suggestions like -r and -f with userdel guarantees the person account is totally deleted even though the person is logged in or has energetic processes.
50. groupadd â Upload A Crew
The groupadd command creates a brand new person crew. Teams constitute groups or roles for permissions functions.
As an example:
groupadd -r sysadmin
Helpful groupadd suggestions:
-râ Create a formulation crew used for core formulation purposes.-gâ Specify the brand new crewâs GID as an alternative of the usage of subsequent to be had.
The above command creates a brand new âsysadminâ crew with formulation privileges. When growing new teams, the -r or -g lend a hand set them up accurately.
51. passwd â Replace Personâs Authentication Tokens
The passwd command units or updates a personâs authentication password/tokens. This permits converting your login password.
As an example:
passwd john
This activates person âjohnâ to go into a brand new password interactively. If you happen toâve misplaced the password for an account, you could need to login to Linux with sudo or su privileges and alter the password the usage of the similar way.
Networking Instructions
Those instructions are used for tracking connections, troubleshooting community problems, routing, DNS lookups, and interface configuration.
52. ping â Ship ICMP ECHO_REQUEST To Community Hosts
The ping command verifies connectivity to a faraway host through sending ICMP echo request packets and listening for echo responses.
As an example:
ping google.comPING google.com (142.251.42.78): 56 information bytes64 bytes from 142.251.42.78: icmp_seq=0 ttl=112 time=8.590 ms64 bytes from 142.251.42.78: icmp_seq=1 ttl=112 time=12.486 ms64 bytes from 142.251.42.78: icmp_seq=2 ttl=112 time=12.085 ms64 bytes from 142.251.42.78: icmp_seq=3 ttl=112 time=10.866 ms--- google.com ping statistics ---4 packets transmitted, 4 packets gained, 0.0% packet lossround-trip min/avg/max/stddev = 8.590/11.007/12.486/1.518 ms
Helpful ping suggestions:
-c [count]â Restrict packets despatched.-i [interval]â Wait period seconds between pings.
With the above command, you ping google.com and outputs round-trip stats indicating connectivity and latency. Usually, ping is used to test if a formulation youâre making an attempt to hook up with is alive and attached to the community.
53. ifconfig â Configure Community Interfaces
The ifconfig command shows and configures community interface settings, together with IP cope with, netmask, broadcast, MTU, and {hardware} MAC cope with.
As an example:
ifconfigeth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500inet 10.0.2.15 netmask 255.255.255.0 broadcast 10.0.2.255inet6 fe80::a00:27ff:fe1e:ef1d prefixlen 64 scopeid 0x20<hyperlink>ether 08:00:27:1e:ef:1d txqueuelen 1000 (Ethernet)RX packets 23955654 bytes 16426961213 (15.3 GiB)RX mistakes 0 dropped 0 overruns 0 body 0TX packets 12432322 bytes 8710937057 (8.1 GiB)TX mistakes 0 dropped 0 overruns 0 service 0 collisions 0
Operating ifconfig and not using a different arguments will provide you with an inventory of all of the community interfaces to be had to be used, along side IP and extra community knowledge. ifconfig may also be used to set addresses, permit/disable interfaces, and alter suggestions.
54. netstat â Community Statistics
The netstat command displays you the community connections, routing tables, interface stats, masquerade connections, and multicast memberships.
As an example:
netstat -pt tcp
This command will output all of the energetic TCP connections and the processes the usage of them.
55. ss â Socket Statistics
The ss command dumps socket statistical knowledge very similar to netstat. It may well display open TCP and UDP sockets, ship/obtain buffer sizes, and extra.
As an example:
ss -t -a
This prints all open TCP sockets. Extra environment friendly than netstat.
56. traceroute â Hint Path To Host
The traceroute command prints the path packets take to a community host, appearing every hop alongside the way in which and transit occasions. Helpful for community debugging.
As an example:
traceroute google.com
This lines the trail to achieve google.com and outputs every community hop.
57. dig - DNS Look up
The dig command plays DNS lookups and returns details about DNS information for a website.
As an example:
dig google.com; <<>> DiG 9.10.6 <<>> google.com;; world suggestions: +cmd;; Were given solution:;; ->>HEADER<<- opcode: QUERY, standing: NOERROR, identity: 60290;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1;; OPT PSEUDOSECTION:; EDNS: model: 0, flags:; udp: 1280;; QUESTION SECTION:;google.com. IN A;; ANSWER SECTION:google.com. 220 IN A 142.251.42.78;; Question time: 6 msec;; SERVER: 2405:201:2:e17b::c0a8:1d01#53(2405:201:2:e17b::c0a8:1d01);; WHEN: Wed Nov 15 01:36:16 IST 2023;; MSG SIZEÂ rcvd: 55
This queries DNS servers for information associated with google.com and prints main points.
58. nslookup â Question Web Title Servers Interactively
The nslookup command queries DNS servers interactively to accomplish identify solution lookups or show DNS information.
It enters an interactive shell, permitting you to manually look up hostnames, opposite IP addresses, in finding DNS file sorts, and extra.
As an example, some commonplace nslookup utilization. Sort nslookup in your command line:
nslookup
Subsequent, weâll set Googleâs 8.8.8.8 DNS server for lookups.
> server 8.8.8.8
Now, letâs question the A file of stackoverflow.com to seek out its IP cope with.
> set form=A> stackoverflow.comServer: 8.8.8.8Deal with: 8.8.8.8#53Non-authoritative solution:Title: stackoverflow.comDeal with: 104.18.32.7Title: stackoverflow.comDeal with: 172.64.155.249
Now, letâs in finding the MX information for github.com to look its mail servers.
> set form=MX> github.comServer: 8.8.8.8Deal with: 8.8.8.8#53Non-authoritative solution:github.com mail exchanger = 1 aspmx.l.google.com.github.com mail exchanger = 5 alt1.aspmx.l.google.com.github.com mail exchanger = 5 alt2.aspmx.l.google.com.github.com mail exchanger = 10 alt3.aspmx.l.google.com.github.com mail exchanger = 10 alt4.aspmx.l.google.com.
The interactive queries make nslookup very helpful for exploring DNS and troubleshooting identify solution problems.
59. iptables â IPv4 Packet Filtering And NAT
The iptables command permits configuring Linux netfilter firewall regulations to filter out and procedure community packets. It units up insurance policies and regulations for the way the formulation will deal with several types of inbound and outbound connections and site visitors.
As an example:
iptables -A INPUT -s 192.168.1.10 -j DROP
The above command will block all enter from IP 192.168.1.10.
iptables supplies robust regulate over the Linux kernel firewall to deal with routing, NAT, packet filtering, and different site visitors regulate. This can be a important software for securing Linux servers.
60. ip â Arrange Community Gadgets And Routing
The ip command permits managing and tracking more than a few community machine linked actions like assigning IP addresses, putting in subnets, exhibiting hyperlink main points, and configuring routing suggestions.
As an example:
ip hyperlink display1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN mode DEFAULT crew default qlen 1000hyperlink/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:002: eth0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UP mode DEFAULT crew default qlen 1000hyperlink/ether 08:00:27:8a:5c:04 brd ff:ff:ff:ff:ff:ff
The above command displays all of the community interfaces, their standing, and different knowledge.
This command targets to exchange ifconfig with extra fashionable Linux community control. ip can regulate community units, routing tables, and different community stack settings.
Bundle Control Instructions
Bundle managers permit simple set up, replace and elimination of device on Linux distributions. Standard package deal managers come with APT, YUM, DNF, Pacman, and Zypper.
61. apt â Debian/Ubuntu Bundle Supervisor
The apt command manages applications on Debian/Ubuntu methods the usage of the APT repository. It permits putting in, updating, and taking away applications.
As an example:
apt replace
This command fetches the newest package deal variations and metadata from the repositories.
apt set up nginx
You’ll set up the nginx package deal from the configured APT repositories the usage of the above command.
apt improve
And this command upgrades applications and dependencies to more recent variations.
APT makes putting in device simple through fetching applications from repositories.
62. pacman â Arch Linux Bundle Supervisor
pacman manages applications on Arch Linux from the Arch Person Repository. It may well set up, improve, and take away applications.
As an example:
pacman -S nmap
This installs the nmap package deal from the configured repositories.
pacman -Syu
This synchronizes with repositories and upgrades all applications.
pacman helps to keep Arch Linux up-to-date and permits simple control of applications.
63. dnf â Fedora Bundle Supervisor
dnf installs, updates, and gets rid of applications on Fedora Linux distributions the usage of RPM applications. It replaces Yum because the next-gen package deal supervisor.
As an example:
dnf set up util-linux
This installs the util-linux package deal.
dnf improve
This upgrades all put in applications to the newest variations.
dnf makes Fedora package deal control rapid and environment friendly.
64. yum â Pink Hat Bundle Supervisor
yum manages applications on RHEL and CentOS Linux distributions the usage of RPM applications. It fetches from Yum repositories to put in and replace.
As an example:
yum replace
This updates all put in applications to the newest variations.
yum set up httpd
The above command installs the Apache httpd package deal. yum has been the most important package deal supervisor for maintaining Pink Hat distributions up to date.
65. zypper â OpenSUSE Bundle Supervisor
zypper manages applications on SUSE/openSUSE Linux. It may well upload repositories, seek, set up, and improve applications.
As an example:
zypper refresh
The refresh command for zypper refreshes repository metadata from added repositories.
zypper set up python
This installs the Python package deal from configured repositories. zypper makes the package deal control enjoy easy on SUSE/openSUSE methods.
66. flatpak â Flatpak Software Bundle Supervisor
The flatpak command is helping you handle Flatpak programs and runtimes. flatpak permits sandboxed desktop utility distribution throughout Linux.
As an example:
flatpak set up flathub org.libreoffice.LibreOffice
For example, the above command will set up LibreOffice from the Flathub repository.
flatpak run org.libreoffice.LibreOffice
And this one launches the sandboxed LibreOffice Flatpak utility. flatpak supplies a centralized cross-distro Linux utility repository so that youâre not restricted to applications to be had with a selected distroâs package deal library.
67. appimage â AppImage Software Bundle Supervisor
AppImage applications are self-contained programs that run on maximum Linux distributions. The appimage command runs current AppImages.
As an example:
chmod +x myapp.AppImage./myapp.AppImage
This permits operating the AppImage binary dossier without delay.
AppImages permit utility deployment with out system-wide set up. Call to mind them like small boxes that come with all of the information to permit the app to run with out too many exterior dependencies.
68. snap â Snappy Software Bundle Supervisor
The snap command manages snapsâcontainerized device applications. Snaps auto-update and paintings throughout Linux distributions very similar to Flatpak.
As an example:
snap set up vlc
This straightforward command installs the VLC media participant snap.
snap run vlc
As soon as put in, you’ll use snap to run applications which are put in by way of snap through the usage of the above command. Snaps isolate apps from the bottom formulation for portability and make allowance cleaner installs.
Gadget Data Instructions
Those instructions will let you view information about your Linux formulation {hardware}, kernel, distributions, hostname, uptime, and extra.
69. uname â Print Gadget Data
The uname command prints detailed details about the Linux formulation kernel, {hardware} structure, hostname, and working formulation. This comprises model numbers and system information.
As an example:
uname -aLinux hostname 5.4.0-48-generic x86_64 GNU/Linux
uname comes in handy for querying those core formulation main points. Some suggestions come with:
-aâ Print all to be had formulation information-râ Print simply the kernel free up quantity
The above command revealed prolonged formulation knowledge, together with kernel identify/model, {hardware} structure, hostname, and OS.
uname -r
This will likely print simplest the kernel free up quantity. The uname command displays information about your Linux formulationâs core parts.
70. hostname â Display Or Set The Gadgetâs Host Title
The hostname command prints or units the hostname identifier to your Linux formulation at the community. With out a arguments it shows the present hostname. Passing a reputation will replace the hostname.
As an example:
hostnamelinuxserver
This prints linuxserver â the configured formulation hostname.
hostname UbuntuServer
hostnames establish methods on a community. hostname will get or configures the figuring out identify of your formulation at the community. The second one command is helping you exchange the native hostname to UbuntuServer.
71. uptime â How Lengthy The Gadget Has Been Operating
The uptime command displays how lengthy the Linux formulation has been operating because it was once ultimate rebooted. It prints the uptime and present time.
Merely run the next command to get your formulation uptime information:
uptime23:51:26 up 2 days, 4:12, 1 person, load reasonable: 0.00, 0.01, 0.05
This prints the formulation uptime appearing how lengthy the formulation has been on since ultimate boot.
72. whoami â Print Energetic Person ID
The whoami command prints the efficient username of the present person logged into the formulation. It shows the privilege degree you’re working at.
Sort the command to your terminal to get the ID:
whoamijohn
This prints the efficient username that the present person is logged in and working as and comes in handy in scripts or diagnostics to spot what person account movements are being carried out as.
73. identity â Print Actual And Efficient Person And Crew IDs
The identity command prints detailed person and crew details about the efficient IDs and names of the present person. This comprises:
- Actual person ID and identify.
- Efficient person ID and identify.
- Actual crew ID and identify.
- Efficient crew ID and identify.
To make use of the identity command, merely form:Â
identityuid=1000(john) gid=1000(john) teams=1000(john),10(wheel),998(builders)
The identity command prints the present personâs genuine and efficient person and crew IDs. identity shows person and crew main points helpful for figuring out dossier get admission to permissions.
74. lscpu â Show CPU Structure Data
The lscpu command displays detailed CPU structure knowledge, together with:
- Collection of CPU cores
- Collection of sockets
- Style identify
- Cache sizes
- CPU frequency
- Deal with sizes
To make use of the lscpu command, merely form:Â
lscpuStructure:Â Â Â Â x86_64CPU op-mode(s):Â Â Â 32-bit, 64-bitByte Order:Â Â Â Â Â Little EndianCPU(s):Â Â Â Â Â Â Â 16Online CPU(s) record: 0-15
lscpu main points the CPU structure just like the collection of cores, sockets, style identify, caches, and extra.
75. lsblk â Checklist Block Gadgets
The lsblk command lists details about all to be had block units, together with native disks, walls, and logical volumes. The output comprises machine names, labels, sizes, and mount issues.
lsblkNAME  MAJ:MIN RM  SIZE RO TYPE MOUNTPOINTsda    8:0  0  1.8T 0 disk|-sda1  8:1  0  512M 0 phase /boot|-sda2  8:2  0  16M 0 phase`-sda5  8:5  0  1.8T 0 phase`-lvm1 254:0  0  1.8T 0 lvm  /
lsblk lists all of the block units, together with disks, walls, and logical volumes. Provides an summary of garage units.
76. lsmod â Display The Standing of Modules In The Linux Kernel
The lsmod command prints lately loaded kernel modules like machine drivers. This comprises networking, garage, and different hardware-related modules being utilized by the Linux kernel to interface with inner and exterior units.
lsmodModule         Dimension Utilized byipv6         406206 27evdev          17700 0crct10dif_pclmul    16384 1crc32_pclmul      16384 0ghash_clmulni_intel  16384 0aesni_intel      399871 0aes_x86_64       20274 1 aesni_intel
As you’ll see, it lists the lately loaded kernel modules like machine drivers. On this case, it displays the usage of networking, enter, cryptographic and encryption modules.
77. dmesg â Print Or Regulate The Kernel Ring Buffer
The dmesg command dumps messages from the kernel ring buffer. This comprises very important formulation occasions recorded through the kernel all over start-up and operation.
dmesg | grep -i error[ Â 12.345678] Error receiving batched learn reaction: -110[ Â 23.456789] tplink_mdio 0000:03:00.0: Direct firmware load for tplink-mdio/leap_p8_v1_0.bin failed with error -2[ Â 40.567890] iwlwifi 0000:09:00.0: Direct firmware load for iwlwifi-ty-a0-gf-a0-59.ucode failed with error -2
Grepping for âerrorâ displays problems loading explicit firmware. This prints buffered kernel log messages, together with formulation occasions like start-up, mistakes, warnings and many others.
Gadget Management Instructions
Gadget admin instructions allow you to run methods as different customers, close down or reboot the formulation, and handle init methods and products and services.
78. sudo â Execute A Command As Any other Person
The sudo command lets you run instructions as some other person, normally the superuser. After coming into the sudo order, it’s going to instructed you to your password to authenticate.
This offers increased get admission to for duties like putting in applications, enhancing formulation information, administering products and services and many others.
As an example:
sudo adduser bob[sudo] password for john:
Person âbobâ has been added to the formulation.
This makes use of sudo to create a brand new person, âbobâ. Common customers normally can’t upload customers with out sudo.
79. su â Exchange Person ID Or Change into Superuser
The su command lets you transfer to some other person account together with the superuser. You should give you the goal personâs password to authenticate. This provides direct get admission to to run instructions in some other personâs setting.
As an example:
su bobPassword:bob@linux:~$
After inputting bobâs password, this command switches the present person to the person âbobâ. The shell instructed will mirror the brand new person.
80. shutdown â Shutdown Or Restart Linux
The shutdown command schedules a formulation energy off, halt or reboot after a specified timer or in an instant. Itâs required to reboot or shutdown multi-user Linux methods safely.
As an example:
shutdown -r nowBroadcast message from root@linux Fri 2023-01-20 18:12:37 CST:The formulation is taking place for reboot NOW!
This reboots the formulation immediately with a caution to customers.
81. reboot â Reboot Or Restart Gadget
The reboot command restarts the Linux working formulation, logging all customers off and safely rebooting the formulation. It synchronizes disks and brings the formulation down cleanly ahead of restarting.
As an example:
rebootRestarting formulation.
This in an instant reboots the OS. reboot is an easy choice to shutdown -r.
82. systemctl â Regulate The systemd Gadget And Carrier Supervisor
The systemctl command lets you handle systemd products and services like beginning, preventing, restarting, or reloading them. Systemd is the brand new init formulation utilized in most present Linux distros, changing SysV init.
As an example:
systemctl birth apache2==== AUTHENTICATING FOR org.freedesktop.systemd1.manage-units ===Authentication is needed to start out 'apache2.provider'.Authenticating as: Person TitlePassword:==== AUTHENTICATION COMPLETE ===
This begins the apache2 provider after authenticating.
83. provider â Run A Gadget V Init Script
The provider command runs Gadget V init scripts for controlling products and services. This permits beginning, preventing, restarting, and reloading products and services controlled beneath conventional SysV init.
As an example:
provider iptables birth[ ok ] Beginning iptables (by way of systemctl): iptables.provider.
The above command begins the iptables firewall provider the usage of its SysV init script.
Different Linux Instructions To Take a look at
-
mountâ Mount or âconnectâ drives to the formulation. -
umountâ Umount or âtake awayâ drives from the formulation. -
xargsâ Builds and executes instructions supplied thru usual enter. -
aliasâ Create shortcuts for lengthy or complicated instructions. -
jobsâ Checklist methods lately operating jobs within the background. -
bgâ Resume a stopped or paused background procedure. -
killallâ Terminate processes through program identify relatively than PID. -
historical pastâ Show up to now used instructions throughout the present terminal consultation. -
guyâ Get entry to lend a hand manuals for instructions proper throughout the terminal. -
display screenâ Arrange a couple of terminal periods from a unmarried window. -
sshâ Determine safe encrypted connections to faraway servers. -
tcpdumpâ Seize community site visitors in keeping with explicit standards. -
watchâ Repeat a command at periods and spotlight output variations. -
tmuxâ Terminal multiplexer for power periods and splitting. -
ncâ Open TCP or UDP connections for checking out and information switch. -
nmapâ Host discovery, port scanning, and OS fingerprinting. -
straceâ Debug processes through tracing working formulation alerts and calls.
7 Key Pointers For The use of Linux Instructions
- Know your shell: Bash, zsh, fish? Other shells have distinctive options. Pick out the person who fits your wishes the most productive.
- Grasp the core utils:
ls,cat,grep,sed,awk, and many others shape the core of a Linux toolkit. - Keep on with pipelines: Keep away from over the top makes use of of brief information. Pipe methods in combination cleverly.
- Check ahead of overwriting: At all times double take a look at ahead of overwriting information with
>and>>. - Monitor your workflows: Report complicated instructions and workflows to reuse or proportion later.
- Make your personal gear: Write easy shell scripts and aliases for common duties.
- Get started with out
sudo: Use an ordinary person account to begin with to know permissions.
And take into account to stay checking out out new instructions over digital machines or VPS servers in order that they turn out to be 2d nature to you ahead of you birth the usage of them on manufacturing servers.
VPS Webhosting
A Digital Non-public Server (VPS) is a digital platform that shops information. Many internet hosts be offering VPS web hosting plans, which offer website house owners a devoted, non-public house on a shared server.
Higher Linux Webhosting With DreamHost
After you grasp the very important Linux instructions, you additionally want a web hosting and server supplier that will give you complete regulate to profit from Linuxâs energy and versatility.
Thatâs the place DreamHost shines.
DreamHostâs optimized Linux infrastructure is highest for operating your apps, websites, and products and services:
- Speedy internet web hosting on fashionable Linux servers.
- SSH shell get admission to for command line regulate.
- Customizable PHP variations together with PHP 8.0.
- Apache or NGINX internet servers.
- Controlled MySQL, PostgreSQL, Redis databases.
- 1-click installs of apps like WordPress and Drupal.
- SSD-accelerated NVMe garage for pace.
- Unfastened Letâs Encrypt SSL auto-renewal.
DreamHostâs professionals let you get probably the most out of the Linux platform. Our servers are meticulously configured for safety, efficiency, and reliability.
Release your subsequent venture on a Linux web hosting platform you’ll agree with. Get began with tough, scalable web hosting at DreamHost.com.
Get Content material Delivered Directly to Your Inbox
Subscribe to our weblog and obtain nice content material identical to this delivered immediately in your inbox.